KYA Strategy
The system provides built-in strategies. Users should check whether these meet business needs before enabling or modifying them. Tracing MethodStarting from the target address, transactions are traced both forward and backward to build a complete relationship graph. The application layer will only display parts that match the user’s strategy. Scoring Calculation
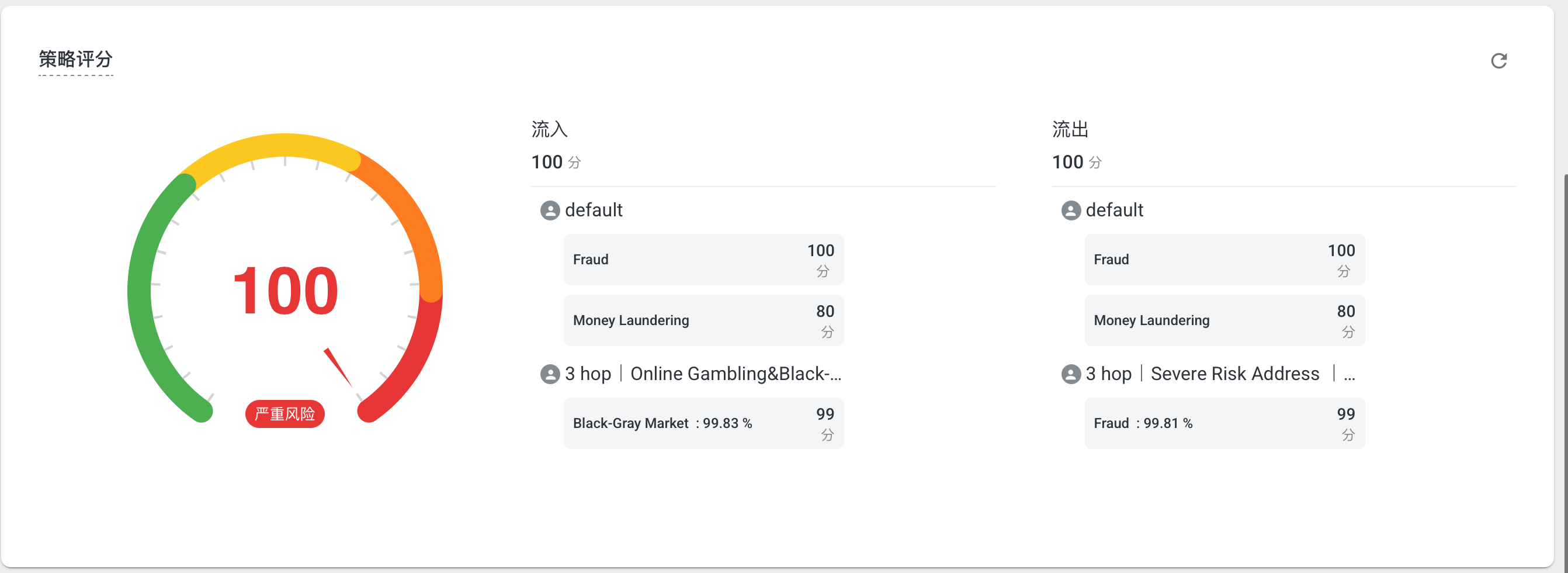
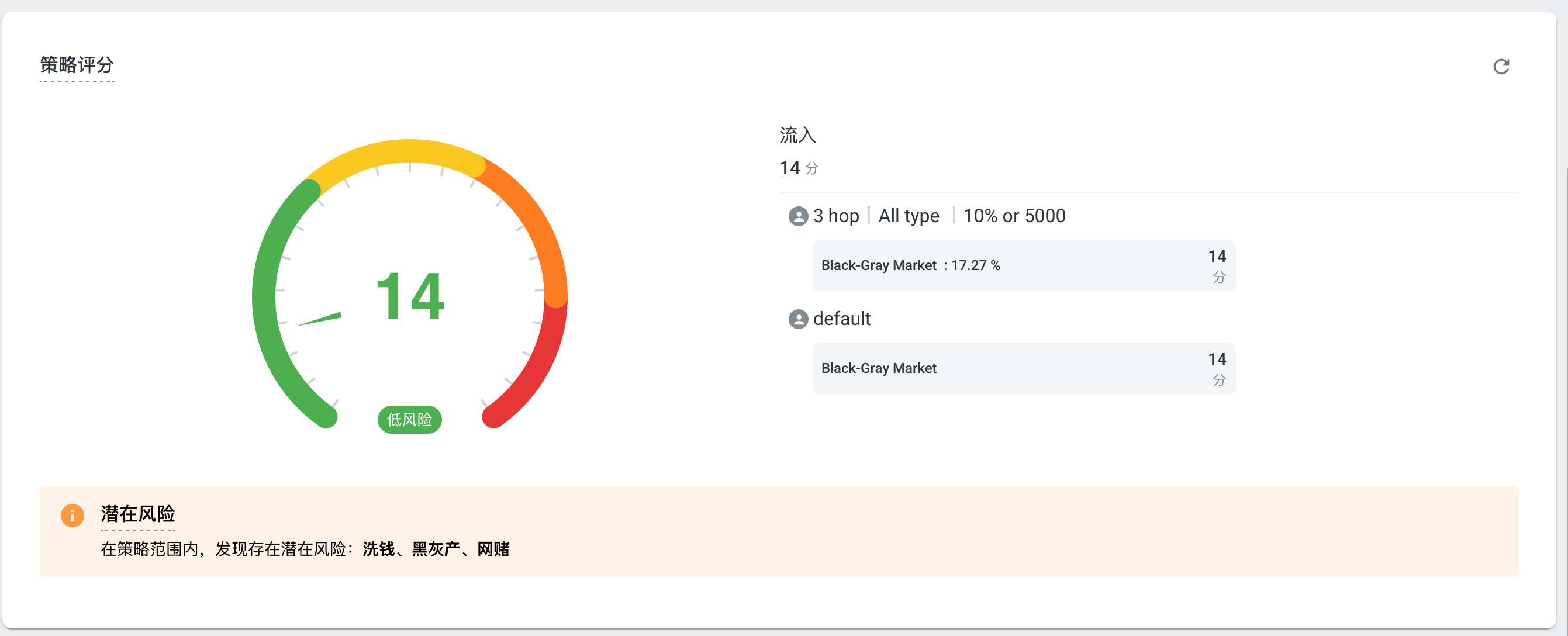
Scores are calculated from the labeled transaction graph based on the user’s scoring rules. When calculating inflows to the target address, scores are diluted proportionally by the share of risky addresses at each level. Strategy Configuration
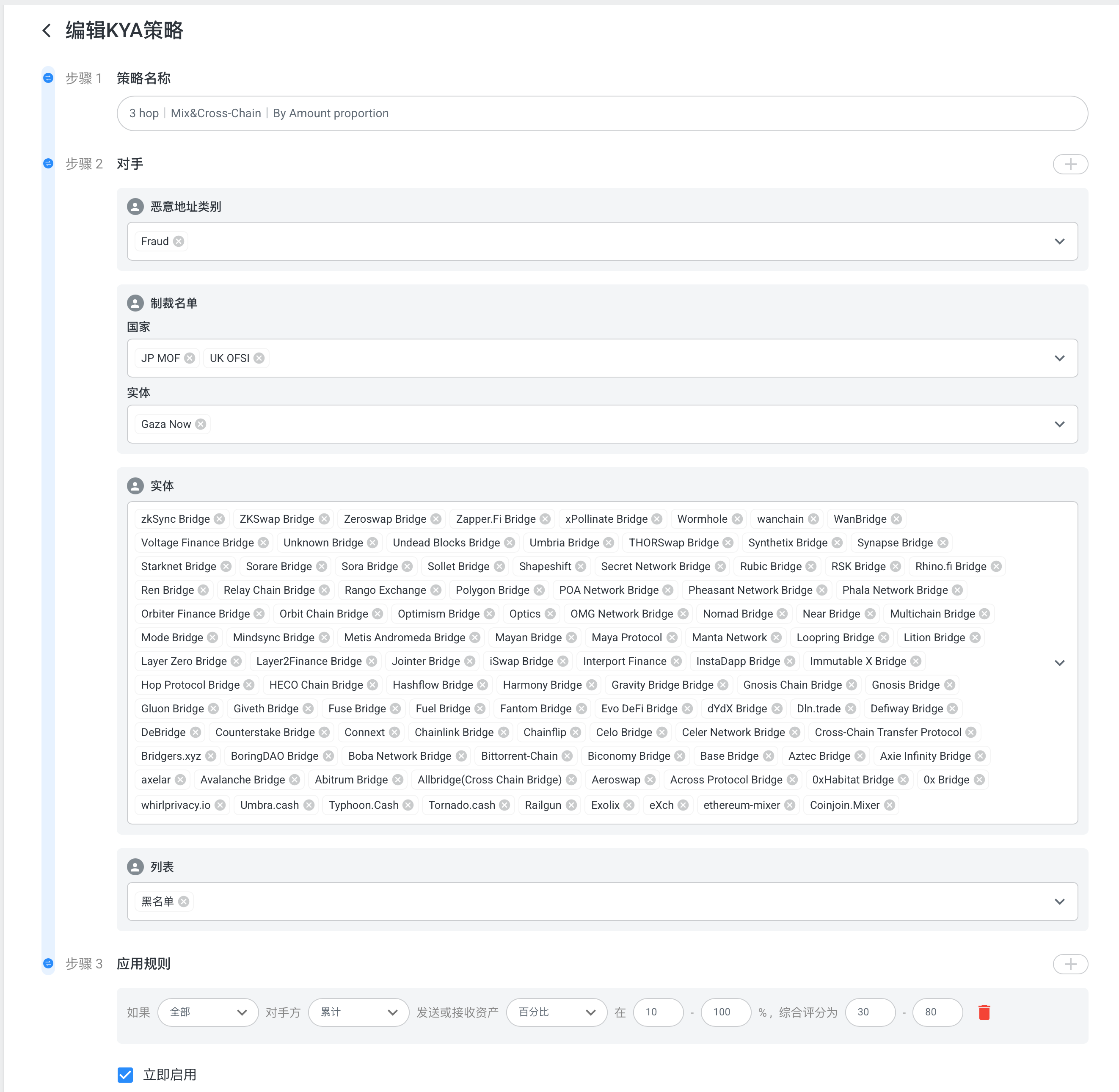
Each strategy must define a tracing scope, with up to 0–6 hops supported.
Required fields for configuration:
- Strategy Name (unique)
- Counterparties: Select from malicious address risk types, sanctioned countries/entities, platform entities, or user-defined black/white lists
- Calculation Rules: Define scoring ranges based on direct/indirect accumulation, sending, or receiving of specific amounts/percentages from these counterparties
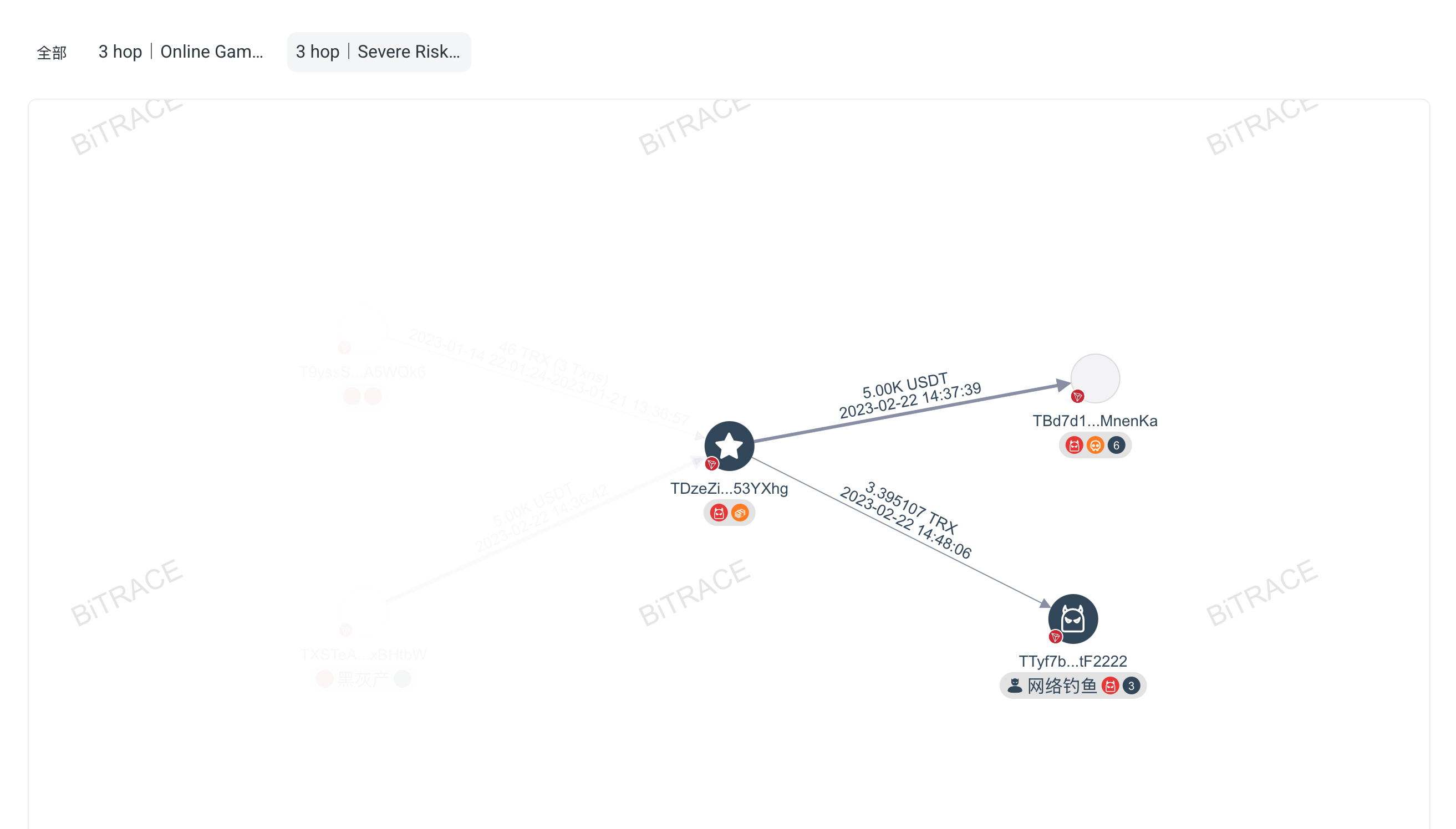
Default Strategy
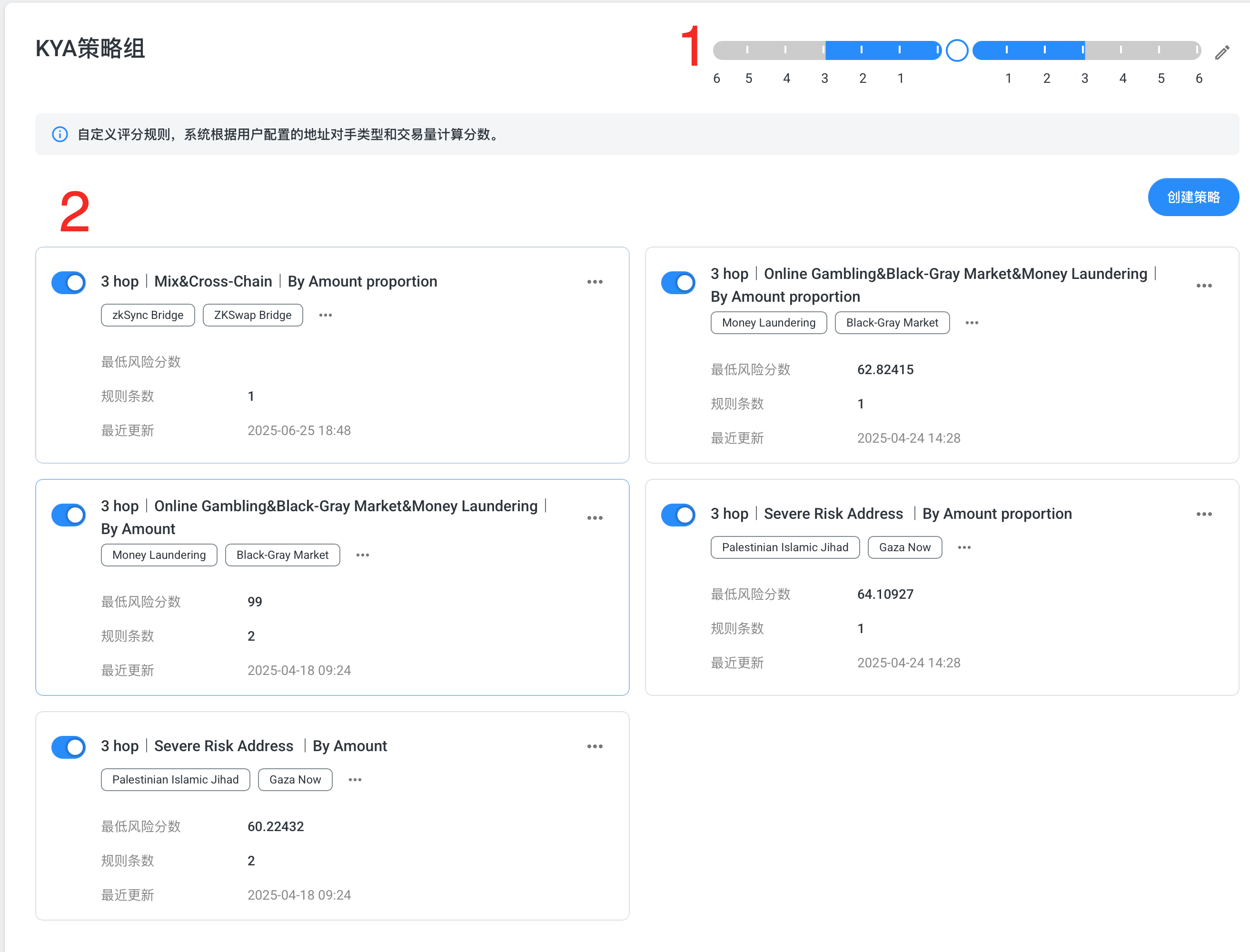
The platform includes one built-in Default strategy that is invisible and unmodifiable by users. This fallback strategy monitors all types of risks to ensure that any risk not covered by user-defined strategies is still detected. The Default strategy focuses only on the types of addresses within the monitored scope and assigns scores based on the type. If an address already has labels, these are directly reflected in the Default strategy. For example, if an address has both Fraud and Money Laundering labels, and the configured type scores are 100 for Fraud and 80 for Money Laundering, the Default strategy will display scores of 100 for Fraud and 80 for Money Laundering. If users consider the Default strategy too strict, they may choose to rely on other strategy scores and ignore the Default score.
KYT Strategy
The usage of KYT strategies is consistent with KYA strategies. When using the strategy module, users should first check whether the platform’s built-in strategies meet their business needs before deciding to enable or modify them.Tracing Method
KYT tracing is based on fund flows. Starting from the target transaction, tracing proceeds only forward. Besides counterparty type, additional stop conditions include dilution amount or dilution proportion. The backend constructs a complete fund flow graph, and the application layer retrieves the risks present in the graph to match strategies and calculate scores.Score Calculation
Scores are calculated based on the counterparty types specified in the user strategy and the actual transaction volume, without requiring the user to configure calculation rules. When calculating the amount flowing into the target address, dilution is applied according to the proportion of risk addresses at each layer.Strategy Configuration
In addition to malicious addresses, sanction lists, and user black/white lists, the built-in strategies also treat “mixers” as stop points. (Underlying tracing already includes exchange entities, so no additional configuration is needed.) Tracing stops when the dilution ratio reaches 10% or when the amount is less than 5,000 USD. (Amounts are in USD because multi-token tracing is performed simultaneously.)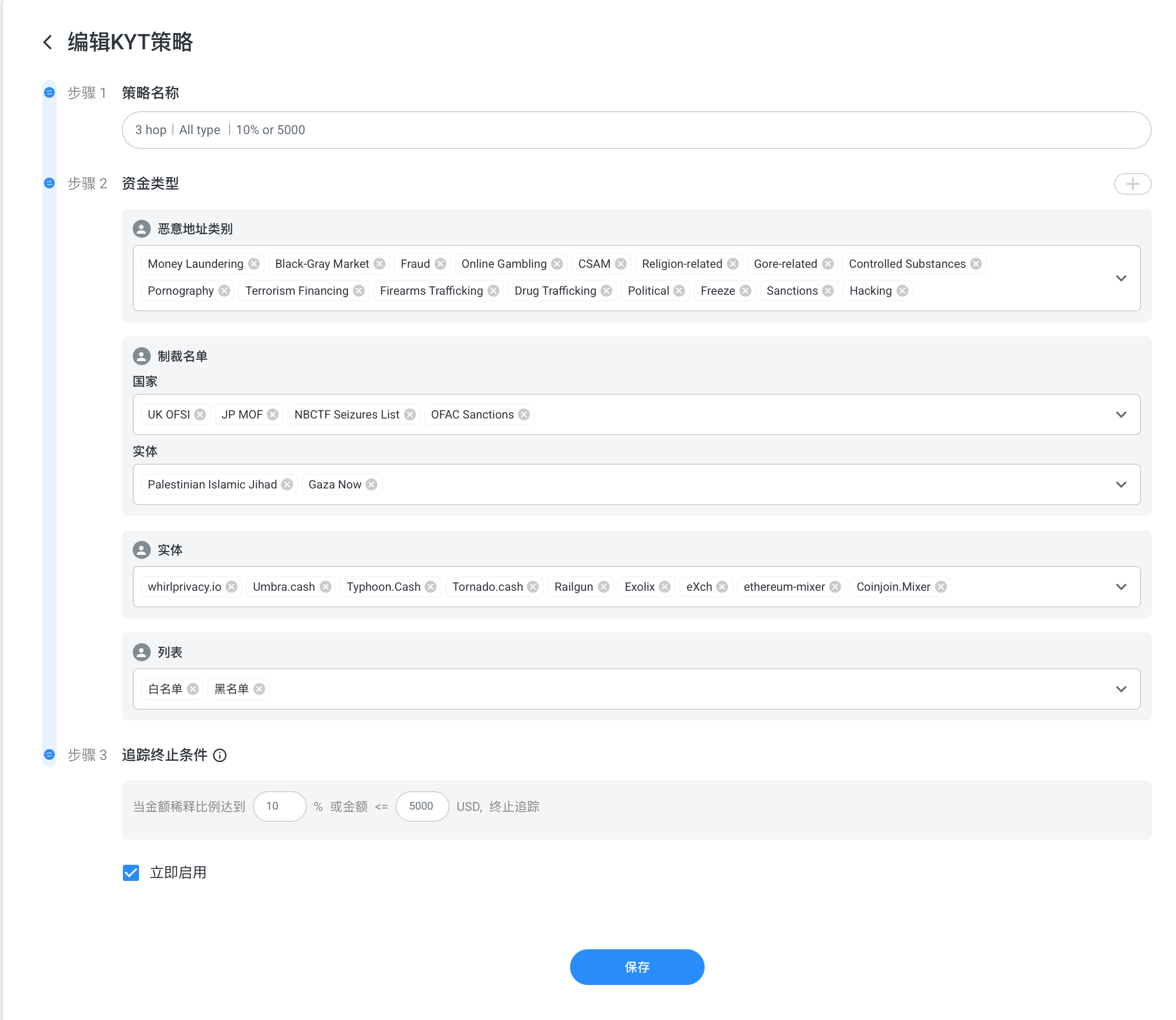
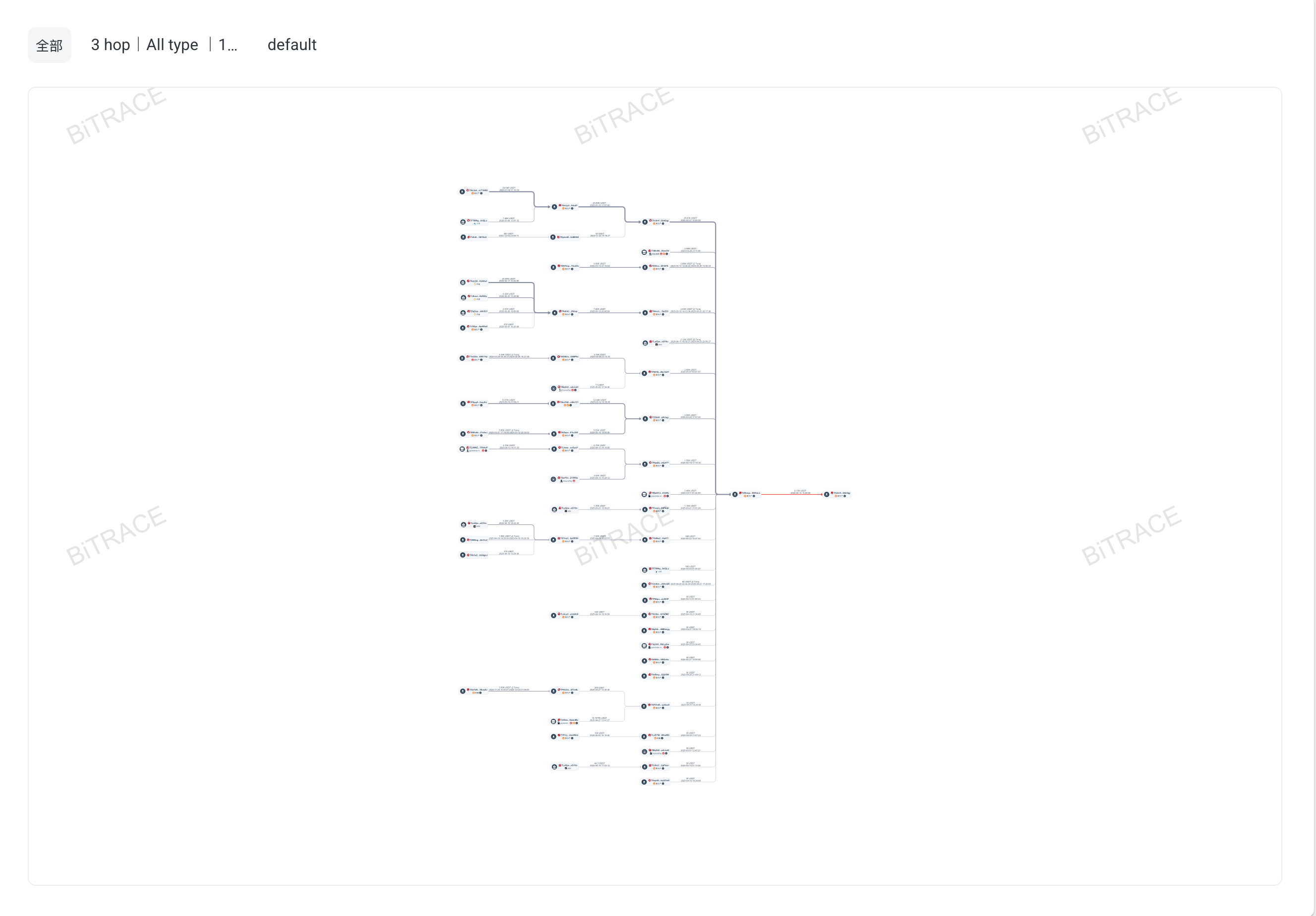
- Tracing stops within 3 hops when any type of address is encountered, or when the traced amount is diluted to 10% or below 5,000 USD.
- Only paths containing source risks are considered. The base risk score of each path is diluted according to the proportion of funds and ultimately applied to the target transaction.
Basic Strategy Configuration
Tokens, address lists, and categories form the fundamental basis for strategy score calculations.Tokens
The table lists the networks and tokens currently supported for tracing:| Network | Tokens | Tracing Range |
|---|---|---|
| ETH | ETH, USDT, USDC | -6, +6 |
| TRON | TRX, USDT | -6, +6 |
| BSC | BNB, USDT | -6, +6 |
| BTC | BTC | -6, +6 |
Address Lists
- Sanctions List: Compiled by the platform based on publicly available national and regional sanctions standards.
- Blacklist: Addresses added by the user. (Assigned a score of 100 in strategies)
- Whitelist: Addresses added by the user. (Assigned a score of 0 in strategies)